
This post was originally published during April of 2019 and updated in July of 2022 and July of 2023. Unfortunately, ransomware continues to proliferate. We’ve updated the post to reflect the current state of ransomware and to help individuals and businesses protect their data.
In today’s interconnected world, where our professional lives revolve around technology, the threat of ransomware looms large. It is a profitable business for cybercriminals, causing billions of dollars in damages. You might not have been subject to a ransomware attack yet, but that may not always be the case—unfortunately, the odds are against you.
This comprehensive guide aims to empower you with the knowledge and strategies needed to prevent and recover from ransomware attacks. With preparation and the latest cybersecurity insights, you can safeguard your digital world.
This post is a part of our ongoing coverage of ransomware. Take a look at our other posts for more information on how businesses can defend themselves against a ransomware attack, and more.
In their 2023 Ransomware Trends Report, Veeam found that only 16% of organizations attacked by ransomware were able to recover without paying a ransom. That means, despite almost every business having backups of some kind, only one in six of them were able to use their backups to resume business operations after an attack. As a cloud storage company where many customers store backups, we think that number should be closer to 100%. That’s why we created this guide—getting that number closer to 100% starts with knowing what you’re up against and putting strategies in place to protect your business.
The Ransomware Threat
In 2022, the FBI’s Internet Crime Complaint Center received 2,385 ransomware complaints with adjusted losses of more than $34.3 million, and those are just the ones that got reported. Cybersecurity Ventures expects that, by 2031, businesses will fall victim to a ransomware attack every other second, up from every 11 seconds in 2021, every 14 seconds in 2019, and every 40 seconds in 2016. This exponential rise in victims translates to nearly $265 billion in ransomware damages by 2031 according to Cybersecurity Ventures.
Individual and average ransom amounts are also reaching new heights. In Q1 2023, the average ransom payment was $327,883, up 55% from Q1 of 2022 ($211,529) according to Coveware, a cyber extortion incident response firm. And, 45% of attacks had an initial demand over $1 million.
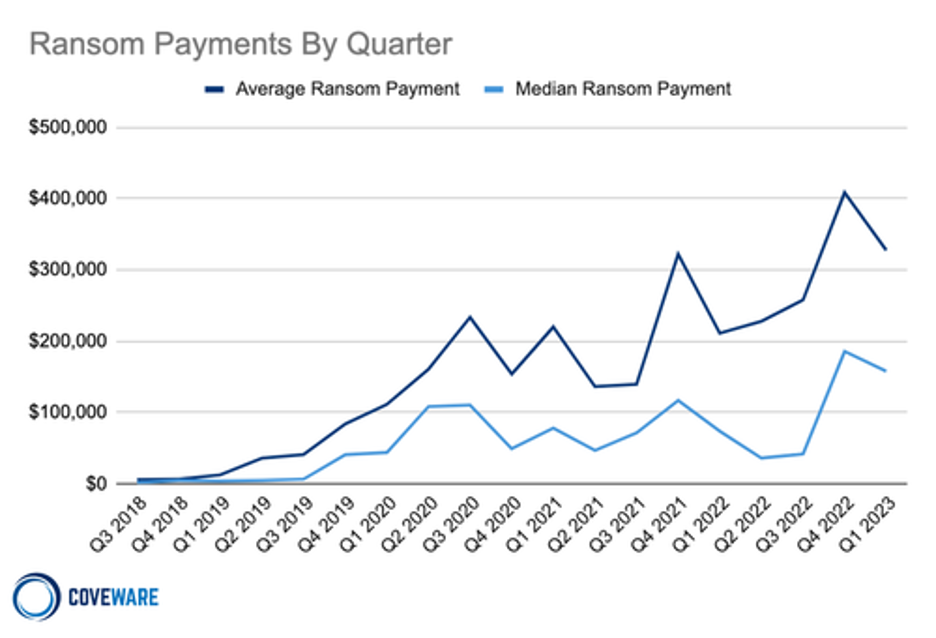
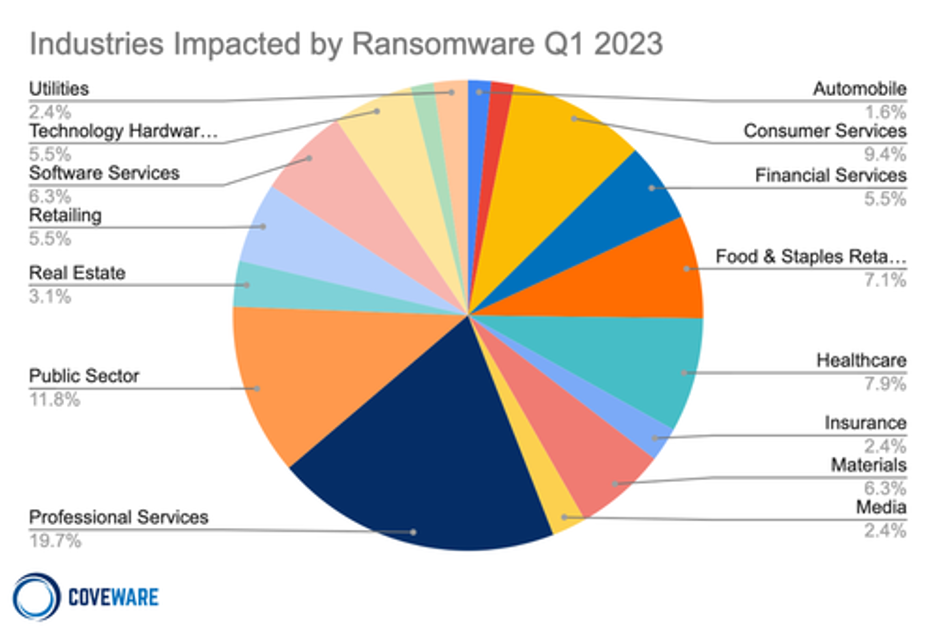
Ransomware affects all industries, from the public sector (state and local government and educational institutions) to healthcare and technology. No group is immune, as seen in the chart below.
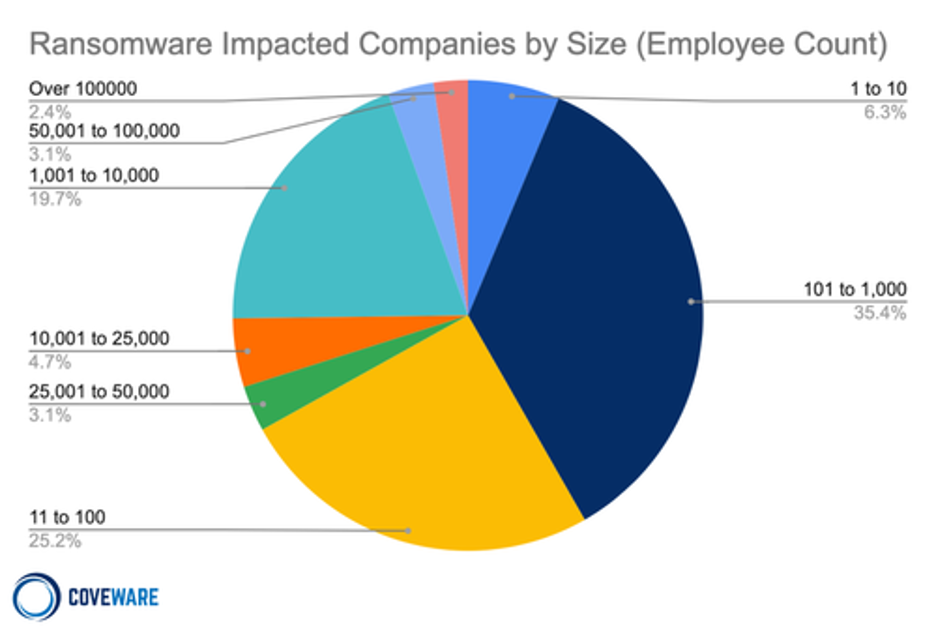
Ransomware continues to be a major threat to businesses in all sectors, but the greatest impact continues to be leveled at small and medium businesses (SMBs). As the table below notes, a vast majority (66.9%) of all the companies impacted by ransomware attacks are SMBs with between 11 and 1,000 employees.
Regardless of your firm’s size, you’ll want to understand how ransomware works, including ransomware as a service (RaaS), as well as how recent developments in generative artificial intelligence (AI) tools are changing the ransomware landscape.
Ransomware as a Service
Ransomware as a Service has emerged as a game changer in the world of cybercrime, revolutionizing the ransomware landscape and amplifying the scale and reach of malicious attacks. The RaaS business model allows even novice cybercriminals to access and deploy ransomware with relative ease, leading to a surge in the frequency and sophistication of ransomware attacks worldwide.
Traditionally, ransomware attacks required a high level of technical expertise and resources, limiting their prevalence to skilled cybercriminals or organized cybercrime groups. However, the advent of RaaS platforms has lowered the barrier to entry, making ransomware accessible to a broader range of individuals with nefarious intent. These platforms provide aspiring cybercriminals with ready-made ransomware toolkits, complete with user-friendly interfaces, step-by-step instructions, and even customer support. In essence, RaaS operates on a subscription or profit-sharing model, allowing criminals to distribute ransomware and share the ransom payments with the RaaS operators.
The rise of RaaS has led to a proliferation of ransomware attacks, with cybercriminals exploiting the anonymity of the dark web to collaborate, share resources, and launch large-scale campaigns. The RaaS model not only facilitates the distribution of ransomware but it also provides criminals with analytics dashboards to track the performance of their campaigns, enabling them to optimize their strategies for maximum profit.
One of the most significant impacts of RaaS is the exponential growth in the number and variety of ransomware strains. RaaS platforms continuously evolve and introduce new ransomware variants, making it increasingly challenging for cybersecurity experts to develop effective countermeasures. The availability of these diverse strains allows cybercriminals to target different industries, geographical regions, and vulnerabilities, maximizing their chances of success.
The profitability of RaaS has attracted a new breed of cybercriminals, leading to an underground economy where specialized roles have emerged. Ransomware developers create and sell their malicious code on RaaS platforms, while affiliates or “distributors” spread the ransomware through various means, such as phishing emails, exploit kits, or compromised websites. This division of labor allows criminals to focus on their specific expertise, while RaaS operators facilitate the monetization process and collect a share of the ransoms.
The impact of RaaS extends beyond the immediate financial and operational consequences for targeted entities. The widespread availability of ransomware toolkits has also resulted in a phenomenon known as “ransomware commoditization,” where cybercriminals compete to offer their services at lower costs or even engage in price wars. This competition drives innovation and the continuous evolution of ransomware, making it a persistent and ever-evolving threat.
To combat the growing influence of RaaS, organizations and individuals require a multilayered approach to cybersecurity. Furthermore, organizations should prioritize data backups and develop comprehensive incident response plans to ensure quick recovery in the event of a ransomware attack. Regularly testing backup restoration processes is essential to maintain business continuity and minimize the impact of potential ransomware incidents.
Ransomware as a Service has profoundly transformed the ransomware landscape, democratizing access to malicious tools and fueling the rise of cybercrime. The ease of use, scalability, and profitability of RaaS platforms have contributed to a surge in ransomware attacks across industries and geographic locations.
Generative AI and Ransomware
The rise of generative AI has been a boon for cybercriminals in helping them automate attacks. If you’ve ever been through any kind of cybersecurity training, you’ll know that spelling mistakes, bad grammar, and awkward writing are some of the most obvious signs of a phishing email. With generative AI, the cybercriminals’ job just got that much easier, and their phishing emails that more convincing.
Now, a cybercriminal just needs to punch a prompt into ChatGPT, and it spits out an error-free, well-written, convincing email that the cybercriminal can use to target victims. It has also been a force multiplier for helping cybercriminals translate that email into different languages or target it to specific industries or even companies. Text generated by models like ChatGPT help cybercriminals create very personalized messages that are more likely to have the desired effect of getting a target to click a malicious link or download a malicious payload.
How Does Ransomware Work?
A ransomware attack starts when a machine on your network becomes infected with malware. Cybercriminals have a variety of methods for infecting your machine, whether it’s an attachment in an email, a link sent via spam, or even through sophisticated social engineering campaigns. As users become more savvy to these attack vectors, cybercriminals’ strategies evolve. Once that malicious file has been loaded onto an endpoint, it spreads to the network, locking every file it can access behind strong encryption controlled by cybercriminals. If you want that encryption key, you’ll have to pay the price.
When we say ‘hacker,’ it’s not some kid in his basement. They’re stealthy, professional crime organizations. They attack slowly and methodically. They can monitor your network for months, until they have the keys to the kingdom—including backups—then they pull the trigger.
—Gregory Tellone, CEO, Continuity Centers
Encrypting ransomware or cryptoware is by far the most common variety of ransomware. Other types that might be encountered are:
- Non-encrypting ransomware or lock screens, which restrict access to files and data, but do not encrypt them.
- Ransomware that encrypts a drive’s master boot record (MBR) or Microsoft’s NTFS, which prevents victims’ computers from being booted up in a live operating system (OS) environment.
- Leakware or extortionware, which steals compromising or damaging data that the attackers then threaten to release if ransom is not paid.
- Mobile device ransomware which infects cell phones through drive-by downloads or fake apps.
What Happens During a Typical Attack?
The typical steps in a ransomware attack are:
- Infection: Ransomware gains entry through various means such as phishing emails, physical media like thumb drives, or alternative methods. It then installs itself on a single endpoint or network device, granting the attacker access.
- Secure Key Exchange: Once installed, the ransomware communicates with the perpetrator’s central command and control server, triggering the generation of cryptographic keys required to lock the system securely.
- Encryption: With the cryptographic lock established, the ransomware initiates the encryption process, targeting files both locally and across the network, rendering them inaccessible without the decryption keys.
- Extortion: Having gained secure and impenetrable access to your files, the ransomware displays an explanation of the next steps, including the ransom amount, instructions for payment, and the consequences of noncompliance.
- Recovery Options: At this stage, the victim can attempt to remove infected files and systems while restoring from a clean backup, or they may consider paying the ransom.
It’s never advised to pay the ransom. According to Veeam’s 2023 Ransomware Trends Report, 21% of those who paid the ransom still were not able to recover their data. There’s no guarantee the decryption keys will work, and paying the ransom only further incentivizes cybercriminals to continue their attacks.
Who Gets Attacked?
Data has shown that ransomware attacks target firms of all sizes, and no business—from small and medium-sized business to large coprorations—is immune. According to the Veeam 2023 Data Protection Trends Report, 85% of organizations suffered at least one cyberattack in the preceding twelve months. Attacks are on the rise in every sector and in every size of business. This leaves small to medium-sized businesses particularly vulnerable, as they may not have the resources needed to shore up their defenses.
Recent attacks where cybercriminals leaked sensitive photos of patients in a medical facility prove that no organization is out of bounds and no victim is off limits. These attempts indicate that organizations which often have weaker controls and out-of-date or unsophisticated IT systems should take extra precautions to protect themselves and their data.
The U.S. consistently ranks highest in ransomware attacks, followed by the U.K. and Germany. Windows computers are the main targets, but ransomware strains exist for Macintosh and Linux, as well.
The unfortunate truth is that ransomware has become so widespread that most companies will certainly experience some degree of a ransomware or malware attack. The best they can do is be prepared and understand the best ways to minimize the impact of ransomware.

Ransomware is more about manipulating vulnerabilities in human psychology than the adversary’s technological sophistication.”
—James Scott, Institute for Critical Infrastructure Technology
How to Combat Ransomware
So, you’ve been attacked by ransomware. Depending on your industry and legal requirements (which, as we have seen, are ever-changing), you may be obligated to report the attack first. Otherwise, your immediate footing should be one of damage control. So what should you do next?
- Isolate the Infection. Swiftly isolate the infected endpoint from the rest of your network and any shared storage to halt the spread of the ransomware.
- Identify the Infection. With numerous ransomware strains in existence, it’s crucial to accurately identify the specific type you’re dealing with. Conduct scans of messages, files, and utilize identification tools to gain a clearer understanding of the infection.
- Report the Incident. While legal obligations may vary, it is advisable to report the attack to the relevant authorities. Their involvement can provide invaluable support and coordination for countermeasures.
- Evaluate Your Options. Assess the available courses of action to address the infection. Consider the most suitable approach based on your specific circumstances.
- Restore and Rebuild. Utilize secure backups, trusted program sources, and reliable software to restore the infected computer or set up a new system from scratch.
1. Isolate the Infection
Depending on the strain of ransomware you’ve been hit with, you may have little time to react. Fast-moving strains can spread from a single endpoint across networks, locking up your data as it goes, before you even have a chance to contain it.
The first step, even if you just suspect that one computer may be infected, is to isolate it from other endpoints and storage devices on your network. Disable Wi-Fi, disable Bluetooth, and unplug the machine from both any local area network (LAN) or storage device it might be connected to. This not only contains the spread but also keeps the ransomware from communicating with the attackers.
Know that you may be dealing with more than just one “patient zero.” The ransomware could have entered your system through multiple vectors, particularly if someone has observed your patterns before they attacked your company. It may already be laying dormant on another system. Until you can confirm, treat every connected and networked machine as a potential host to ransomware.
2. Identify the Infection
Just as there are bad guys spreading ransomware, there are good guys helping you fight it. Sites like ID Ransomware and the No More Ransom! Project help identify which strain you’re dealing with. And knowing what type of ransomware you’ve been infected with will help you understand how it propagates, what types of files it typically targets, and what options, if any, you have for removal and disinfection. You’ll also get more information if you report the attack to the authorities (which you really should).
3. Report to the Authorities
It’s understood that sometimes it may not be in your business’s best interest to report the incident. Maybe you don’t want the attack to be public knowledge. Maybe the potential downside of involving the authorities (lost productivity during investigation, etc.) outweighs the amount of the ransom. But reporting the attack is how you help everyone avoid becoming victimized and help combat the spread and efficacy of ransomware attacks in the future. With every attack reported, the authorities get a clearer picture of who is behind attacks, how they gain access to your system, and what can be done to stop them.
You can file a report with the FBI at the Internet Crime Complaint Center.
There are other ways to report ransomware, as well.
4. Evaluate Your Options
The good news is, you have options. The bad news is that the most obvious option, paying up, is a terrible idea.
Simply giving into cybercriminals’ demands may seem attractive to some, especially in those previously mentioned situations where paying the ransom is less expensive than the potential loss of productivity. Cybercriminals are counting on this.
However, paying the ransom only encourages attackers to strike other businesses or individuals like you. Paying the ransom not only fosters a criminal environment but also leads to civil penalties—and you might not even get your data back.
The other option is to try and remove it.
5. Restore and Rebuild—or Start Fresh
There are several sites and software packages that can potentially remove the ransomware from your system, including the No More Ransom! Project. Other options can be found, as well.
Whether you can successfully and completely remove an infection is up for debate. A working decryptor doesn’t exist for every known ransomware. The nature of the beast is that every time a good guy comes up with a decryptor, a bad guy writes new ransomware. To be safe, you’ll want to follow up by either restoring your system or starting over entirely.
Why Starting Over Using Your Backups Is the Better Idea
The surest way to confirm ransomware has been removed from a system is by doing a complete wipe of all storage devices and reinstalling everything from scratch. Formatting the hard disks in your system will ensure that no remnants of the ransomware remain.
To effectively combat the ransomware that has infiltrated your systems, it is crucial to determine the precise date of infection by examining file dates, messages, and any other pertinent information. Keep in mind that the ransomware may have been dormant within your system before becoming active and initiating significant alterations. By identifying and studying the specific characteristics of the ransomware that targeted your systems, you can gain valuable insights into its functionality, enabling you to devise the most effective strategy for restoring your systems to their optimal state.
Select a backup or backups that were made prior to the date of the initial ransomware infection. If you’ve been following a sound backup strategy, you should have copies of all your documents, media, and important files right up to the time of the infection. With both local and off-site backups, you should be able to use backup copies that you know weren’t connected to your network after the time of attack, and hence, protected from infection. Backup drives that were completely disconnected should be safe, as are files stored in the cloud, especially if you use Object Lock to make them immutable.
How Object Lock Protects Your Data
Object Lock functionality for backups allows you to store objects using a write once, read many (WORM) model, meaning that after it’s written, data cannot be modified. Using Object Lock, no one can encrypt, tamper with, or delete your protected data for a specified period of time, creating a solid line of defense against ransomware attacks.
Object Lock creates a virtual air gap for your data. The term air gap comes from the world of LTO tape. When backups are written to tape, the tapes are then physically removed from the network, creating a literal gap of air between backups and production systems. In the event of a ransomware attack, you can just pull the tapes from the previous day to restore systems. Object Lock does the same thing, but it all happens in the cloud. Instead of physically isolating data, Object Lock virtually isolates the data.
Object Lock is valuable in a few different use cases:
- To replace an LTO tape system: Most folks looking to migrate from tape are concerned about maintaining the security of the air gap that tape provides. With Object Lock, you can create a backup that’s just as secure as air-gapped tape without the need for expensive physical infrastructure.
- To protect and retain sensitive data: If you work in an industry that has strong compliance requirements—for instance, if you’re subject to HIPAA regulations or if you need to retain and protect data for legal reasons—Object Lock allows you to easily set appropriate retention periods to support regulatory compliance.
- As part of a disaster recovery (DR) and business continuity plan: The last thing you want to worry about in the event you are attacked by ransomware is whether your backups are safe. Being able to restore systems from backups stored with Object Lock can help you minimize downtime and interruptions, comply with cyber insurance requirements, and achieve recovery time objectives (RTO) easier. By making critical data immutable, you can quickly and confidently restore uninfected data from your backups, deploy them, and return to business without interruption.
Ransomware attacks can be incredibly disruptive. By adopting the practice of creating immutable, air-gapped backups using Object Lock functionality, you can significantly increase your chances of achieving a successful recovery. This approach brings you one step closer to regaining control over your data and mitigating the impact of ransomware attacks.
So, Why Not Just Run a System Restore?
While it might be tempting to rely solely on a system restore point to restore your system’s functionality, it is not the best solution for eliminating the underlying virus or ransomware responsible for the initial problem. Malicious software tends to hide within various components of a system, making it impossible for system restore to eradicate all instances.
Another critical concern is that ransomware has the capability to encrypt local backups. If your computer is infected with ransomware, there is a high likelihood that your local backup solution will also suffer from data encryption, just like everything else on the system.
With a good backup solution that is isolated from your local computers, you can easily obtain the files you need to get your system working again. This will also give you the flexibility to determine which files to restore from a particular date and how to obtain the files you need to restore your system.

Human Attack Vectors
Often, the weak link in your security protocol is the ever-elusive X factor of human error. Cybercriminals know this and exploit it through social engineering. In the context of information security, social engineering is the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. In other words, the weakest point in your system is usually somewhere between the keyboard and the chair.
Common human attack vectors include:
1. Phishing
Phishing uses seemingly legitimate emails to trick people into clicking on a link or opening an attachment, unwittingly delivering the malicious payload. The email might be sent to one person or many within an organization, but sometimes the emails are targeted to help them seem more credible. This targeting takes a little more time on the attackers’ part, but the research into individual targets can make their email seem even more legitimate, not to mention the advent of generative AI models like ChatGPT. They might disguise their email address to look like the message is coming from someone the sender knows, or they might tailor the subject line to look relevant to the victim’s job. This highly personalized method is called “spear phishing.”
2. SMSishing
As the name implies, SMSishing uses text messages to get recipients to navigate to a site or enter personal information on their device. Common approaches use authentication messages or messages that appear to be from a financial or other service provider. Even more insidiously, some SMSishing ransomware variants attempt to propagate themselves by sending themselves to all contacts in the device’s contact list.
3. Vishing
In a similar manner to email and SMS, vishing uses voicemail to deceive the victim, leaving a message with instructions to call a seemingly legitimate number which is actually spoofed. Upon calling the number, the victim is coerced into following a set of instructions which are ostensibly to fix some kind of problem. In reality, they are being tricked into installing ransomware on their own computer. Like so many other methods of phishing, vishing has become increasingly sophisticated with sound effects and professional diction that make the initial message and follow-up call seem more legitimate. And like spear phishing, it has become highly targeted.
4. Social Media
Social media can be a powerful vehicle to convince a victim to open a downloaded image from a social media site or take some other compromising action. The carrier might be music, video, or other active content that, once opened, infects the user’s system.
5. Instant Messaging
Between them, IM services like WhatsApp, Facebook Messenger, Telegram, and Snapchat have more than four billion users, making them an attractive channel for ransomware attacks. These messages can seem to come from trusted contacts and contain links or attachments that infect your machine and sometimes propagate across your contact list, furthering the spread.
Machine Attack Vectors
The other type of attack vector is machine to machine. Humans are involved to some extent, as they might facilitate the attack by visiting a website or using a computer, but the attack process is automated and doesn’t require any explicit human cooperation to invade your computer or network.
1. Drive-By
The drive-by vector is particularly malicious, since all a victim needs to do is visit a website carrying malware within the code of an image or active content. As the name implies, all you need to do is cruise by and you’re a victim.
2. System Vulnerabilities
Cybercriminals learn the vulnerabilities of specific systems and exploit those vulnerabilities to break in and install ransomware on the machine. This happens most often to systems that are not patched with the latest security releases.
3. Malvertising
Malvertising is like drive-by, but uses ads to deliver malware. These ads might be placed on search engines or popular social media sites in order to reach a large audience. A common host for malvertising is adults-only sites.
4. Network Propagation
Once a piece of ransomware is on your system, it can scan for file shares and accessible computers and spread itself across the network or shared system. Companies without adequate security might have their company file server and other network shares infected as well. From there, the malware will propagate as far as it can until it runs out of accessible systems or meets security barriers.
5. Propagation Through Shared Services
Online services such as file sharing or syncing services can be used to propagate ransomware. If the ransomware ends up in a shared folder on a home machine, the infection can be transferred to an office or to other connected machines. If the service is set to automatically sync when files are added or changed, as many file sharing services are, then a malicious virus can be widely propagated in just milliseconds.
It’s important to be careful and consider the settings you use for systems that automatically sync, and to be cautious about sharing files with others unless you know exactly where they came from.

Security experts suggest several precautionary measures for preventing a ransomware attack.
- Use antivirus and antimalware software or other security policies to block known payloads from launching.
- Make frequent, comprehensive backups of all important files and isolate them from local and open networks.
- Immutable backup options such as Object Lock offer users a way to maintain truly air-gapped backups. The data is fixed, unchangeable, and cannot be deleted within the time frame set by the end-user.
- Keep offline data backups stored in locations that are air-gapped or inaccessible from any potentially infected computer, such as disconnected external storage drives or the cloud, which prevents the ransomware from accessing them.
- Keep your security up-to-date through trusted vendors of your OS and applications. Remember to patch early and patch often to close known vulnerabilities in operating systems, browsers, and web plugins.
- Consider deploying security software to protect endpoints, email servers, and network systems from infection.
- Exercise good cyber hygiene, exercising caution when opening email attachments and links.
- Segment your networks to keep critical computers isolated and to prevent the spread of ransomware in case of an attack. Turn off unneeded network shares.
- Operate on the principle of least privilege. Turn off admin rights for users who don’t require them. Give users the lowest system permissions they need to do their work.
- Restrict write permissions on file servers as much as possible.
- Educate yourself and your employees in best practices to keep ransomware out of your systems. Update everyone on the latest email phishing scams and human engineering aimed at turning victims into abettors.

It’s clear that the best way to respond to a ransomware attack is to avoid having one in the first place. Other than that, making sure your valuable data is backed up and unreachable to a ransomware infection will ensure that your downtime and data loss will be minimal if you ever fall prey to an attack.
Have you endured a ransomware attack or have a strategy to keep you from becoming a victim? Please let us know in the comments.
Ransomware FAQS
A ransomware attack is a type of cyberattack where cybercriminals or groups gain access to a computer system or network and encrypt valuable files or data, making them inaccessible to the owner. The attackers then demand a ransom, usually in the form of cryptocurrency, in exchange for providing the decryption key to unlock the files. Attackers may also extort victims by exfiltrating and threatening to leak sensitive data. Ransomware attacks can cause significant financial losses, operational disruptions, and potential data breaches if the ransom is not paid or effective countermeasures are not implemented.
Preventing ransomware requires a proactive approach to cybersecurity and cyber resilience. Implement robust security measures, including regularly updating software and operating systems, utilizing strong and unique passwords, and deploying reputable antivirus and antimalware software. Train employees about how to identify phishing and social engineering tactics. Regularly back up critical data to cloud storage, implement tools like Object Lock to create immutability, and test your restoration processes. Lastly, stay informed about the latest threats and security best practices to fortify your defenses against ransomware.
Ransomware gains entry through various means such as phishing emails, physical media like thumb drives, or alternative methods. It then installs itself on one or more endpoints or network devices, granting the attacker access. Once installed, the ransomware communicates with the perpetrator’s central command and control server, triggering the generation of cryptographic keys required to lock the system securely. With the cryptographic lock established, the ransomware initiates the encryption process, targeting files both locally and across the network, and renders them inaccessible without the decryption keys.
Common ransomware attack vectors include malicious email attachments or links, where users unknowingly download or execute the ransomware payload. It can also spread through exploit kits that target vulnerabilities in software or operating systems. Ransomware may propagate through compromised websites, drive-by downloads, or via malicious ads. Additionally, attackers can utilize brute force attacks to gain unauthorized access to systems and deploy ransomware.
WannaCry ransomware is a type of malicious software that emerged in May 2017 and garnered significant attention due to its widespread impact. It operates by exploiting a vulnerability in Microsoft Windows systems, encrypting files on infected computers, and demanding a ransom payment in Bitcoin to restore access. WannaCry spread rapidly across networks, affecting numerous organizations worldwide, including healthcare facilities and government agencies.
First, contain the infection. Isolate the infected endpoint from the rest of your network and any shared storage. Next, identify the infection. With numerous ransomware strains in existence, it’s crucial to accurately identify the specific type you’re dealing with. Conduct scans of messages, files, and utilize identification tools to gain a clearer understanding of the infection. Report the incident. While legal obligations may vary, it is advisable to report the attack to the relevant authorities. Their involvement can provide invaluable support and coordination for countermeasures. Then, assess the available courses of action to address the infection. If you have a solid backup strategy in place, you can utilize secure backups to restore and rebuild your environment.











 Secure Your SaaS Tools: Back Up Microsoft 365 to the Cloud
Secure Your SaaS Tools: Back Up Microsoft 365 to the Cloud